As of today, cyber-attacks at industrial facilities have become more target oriented leading to the loss of finance, both product and equipment collapse, compromised safety and – consequently – it ends with a damaged reputation for a business. This way, it’s fair to conclude that cybersecurity should be considered as a hot topic for each and every CEO, CTO or even a board member. To protect the industrial environment from all possible kinds of cyber threats, professionals are using industrial cybersecurity solutions.
The number of attacks on industrial control systems (ICS) and the operational technology (OT) side of the industrial IoT (IIoT) is growing with alarming frequency. This way, cyber security is a concern for all organisations, no matter the company, industry or country. No wonder that more data protection regulations like the EU GDPR and the California Consumer Privacy Act have appeared to address these issues.
Scott King, Senior Director and Security Advisory Services for Rapid7 states that: “Stuxnet, a malicious computer worm that targeted SCADA (supervisory control and data acquisition) systems in 2010, was a watershed moment for the sector. It showed how a cyber attack can have a serious impact on the physical, as well as the digital, world.”
To make things even worth, there’s a growing cyber talents gap in the industry. Jason Hart, CTO at Gemalto, explains: “There’s no shortage of young people capable of pursuing a career in cyber security. But, the trick is to ensure we nurture their skills and guide them towards using their talents for good, rather than acting as black hat hackers. Thanks to institutions such as GCHQ, initiatives are now being run around the UK that are aimed at producing the next generation of cyber security experts.”

Specialists indicate that more efforts have to be put in both education and training processes. Besides, the cybersecurity industry has to improve its image. It must be regarded as a place where the work is interesting and the salary is good. In general, though, the cybersecurity industry has a serious image problem and currently fails to make careers in cybersecurity seem an interesting and viable option for young professionals.
After all, this kind of shortage doesn’t impact solely the IIoT sector: organizations across the globe are finding it hard to find and employ security professionals. So why is the IIoT so vulnerable to cyberattacks in the first place? Industry analysts and ICS/OT specialists at cybersecurity solutions providers from various countries are quite vocal about it. The list below represents a summary of the major reasons behind the problem.
- Currently, the number of sensors and devices being connected to an organization’s IIoT is gaining ground, and, sadly, that shift contains in itself a huge potential for attackers.
- Simply put: OT equipment and control systems are way outdated. Moreover, they have never been designed for exposure to the Internet and, therefore, they’re dangerously vulnerable in terms of cybersecurity.
- Quite often a Frankenstein-esque mixture of OT and control systems made by multiple vendors isn’t updatable. These systems include human-machine-interface (HMI) computers with access to remote terminal units (RTUs), SCADA master (supervisory control computers), and programmable logic controllers (PLCs).
- Poor (or even lack) of cybersecurity practices and technology or the lack of budgets to do so.
- And – obviously – an escalating number of attacks, variable in their tactics and techniques. The list of cybercriminals now includes sophisticated nation-states, cybercriminals with ransomware for shutting down a plant, and hacktivists.
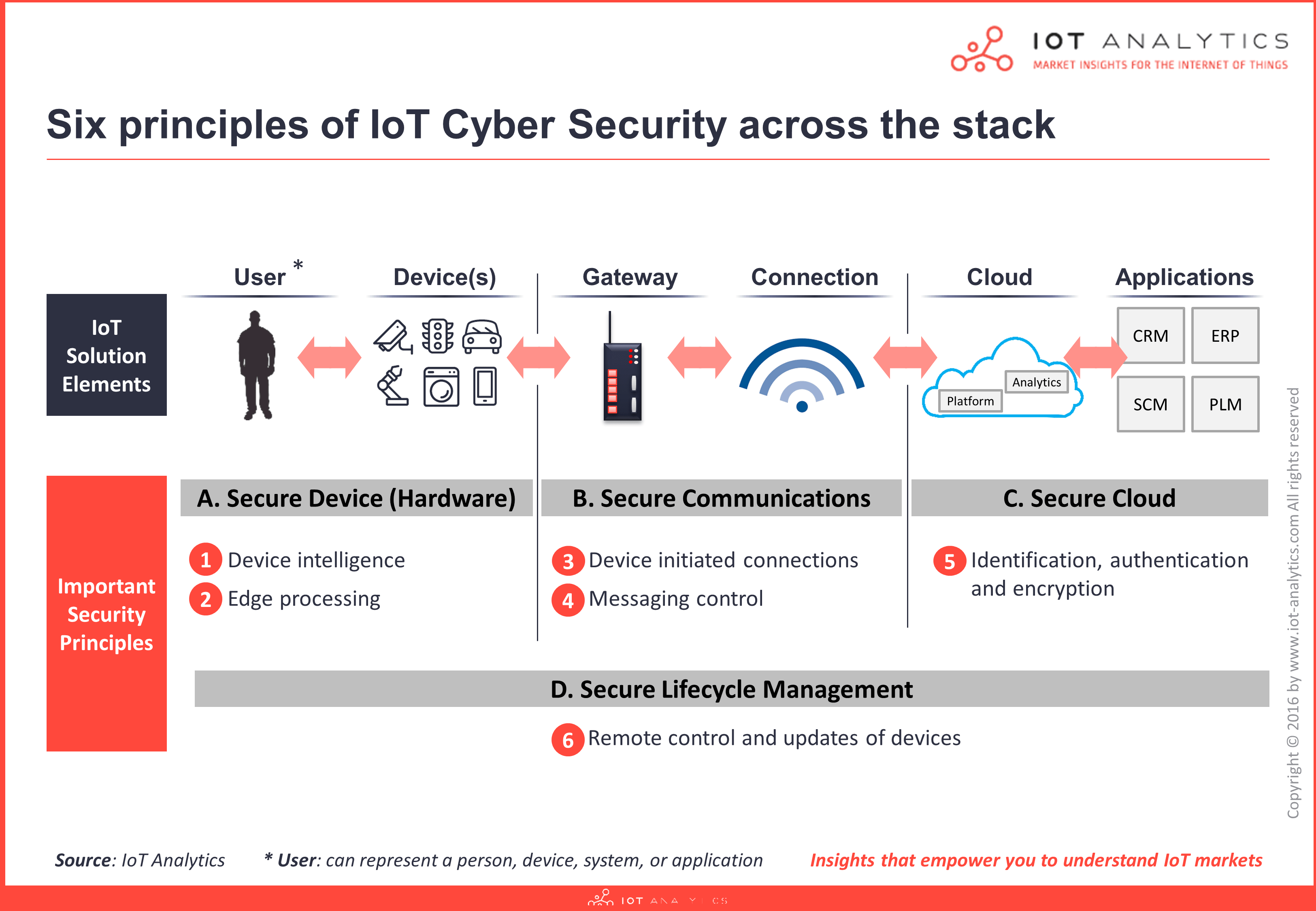
Data breaches represent a significant issue, and the question of privacy has never been more actual than now. This way, if an organisation is thinking about adopting Industry 4.0 working practices, it should begin with studying cyber security practices.
Some of the best methods include:
Credentials
Default usernames and passwords represent a major security risk and tech-savvy attackers use them to get an easy entry point. This way, before you connect a device, it makes perfect sense to start by bringing these credentials to a reset.
Patches
When there’s a code flaw in a software, it is going to be fixed courtesy of the latest updates. This way, institutions must decide how these software patches will be implemented and rolled out to corresponding devices within the environment.
Networks
A complete profile of the network should be taken into consideration. This practice includes the definition of how OT and Industrial Internet of Things (IIoT) are connected and the risk that exists within the process.
The identification of assets
For an organization, it’s critical to understand what processes and assets define its ability to operate to the full. This paradigm makes easier to foresee the potential threat vectors. To get a complete picture, it is recommended to draw a map of processes in a correlation against a network map.
Letting your employees know
Nowadays, the working practices have changed and became more technology-oriented. The key lies within the understanding of how blue-collar workers operate. As employees rely on software to perform their daily tasks, make sure to tell them about the cyber threats they may face. For example, engineers should not be able to just plug in a USB stick without first checking that it is free of malware and its operating system is up to date.

Final thoughts
Sadly enough, but the majority of companies make changes to their security procedures as a sort of reaction to a suffered breach or a cyber attack. This is not the sensible approach. In general, though, cybersecurity has to be considered a collective responsibility within an organization. As they say “forewarned is forearmed”, so make sure to follow the basic practices before it’s too late.